Digital identities are at the center of activity in the digital world.
But fraudulent, stolen, and synthetic identities are fueling daily headlines of online crime and mayhem.
Now imagine reliable identities – if we could have them – as the bedrock of secure and trustworthy activity in the digital world.
We already have them
Measurably reliable identities are a foundational element of the Authenticity Infrastructure, now under development at the Authenticity Institute and being deployed by the enterprises of the Authenticity Alliance.
But how can digital identities be reliable – how can they reliably represent their human counterparts in the physical world?
What is "measurable reliability"?
The human element involved in a claim of identity (“I am John Smith”) is inherently laced with uncertainty – are they telling the truth? What sort of proof or corroboration do they have? – making 100% reliability virtually unattainable.
However, the technology and methods exist now for establishing not certain reliability, but measurable reliability of an identity claim. Measurable reliability means that anyone who is depending upon your digital identity (i.e., is it really you? ) can see a score that measures the reliability of your digital identity. (This doesn't mean the personal reliability of you the human, but rather the confidence level that your digital identity represents the real you.)
How is it measured?
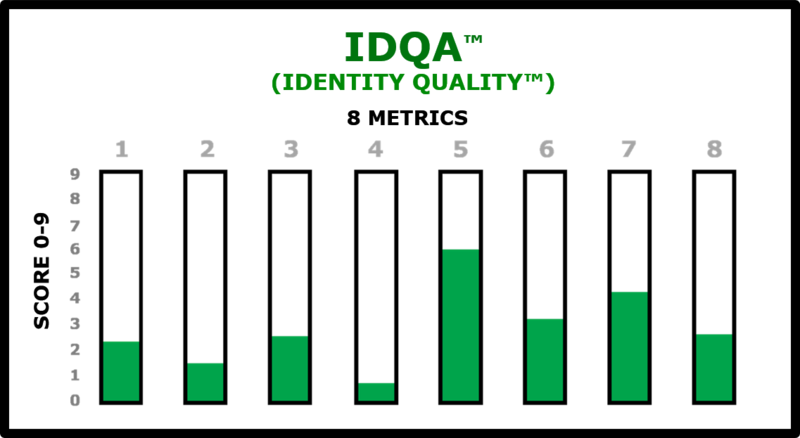
Your identity reliability score (IDQA – Identity Quality Assurance) is a composite of eight metrics that consider such things as evidence of identity, other corroboration, assumption of liability, track record of use, and other contributors to confidence.
Measurably reliable identities are at the heart of Authenticity
Here they are in the definition of Authenticity:

Measurably reliable identities in action
The enterprises of the Authenticity Alliance are putting measurably reliable identities to work solving market-specific problems caused by fraudulent, stolen, and synthetic identities – and problems caused just by the uncertainty of not knowing the trustworthiness of an identity.